A major breach has exposed millions of Gmail passwords, sending shockwaves through global cyber communities. The scale of this incident has activated urgent responses from security experts and affected organisations. The breach entered public view after the release of the Synthient Stealer Log Threat Data, showing 183 million unique email addresses and passwords compromised in April 2025. 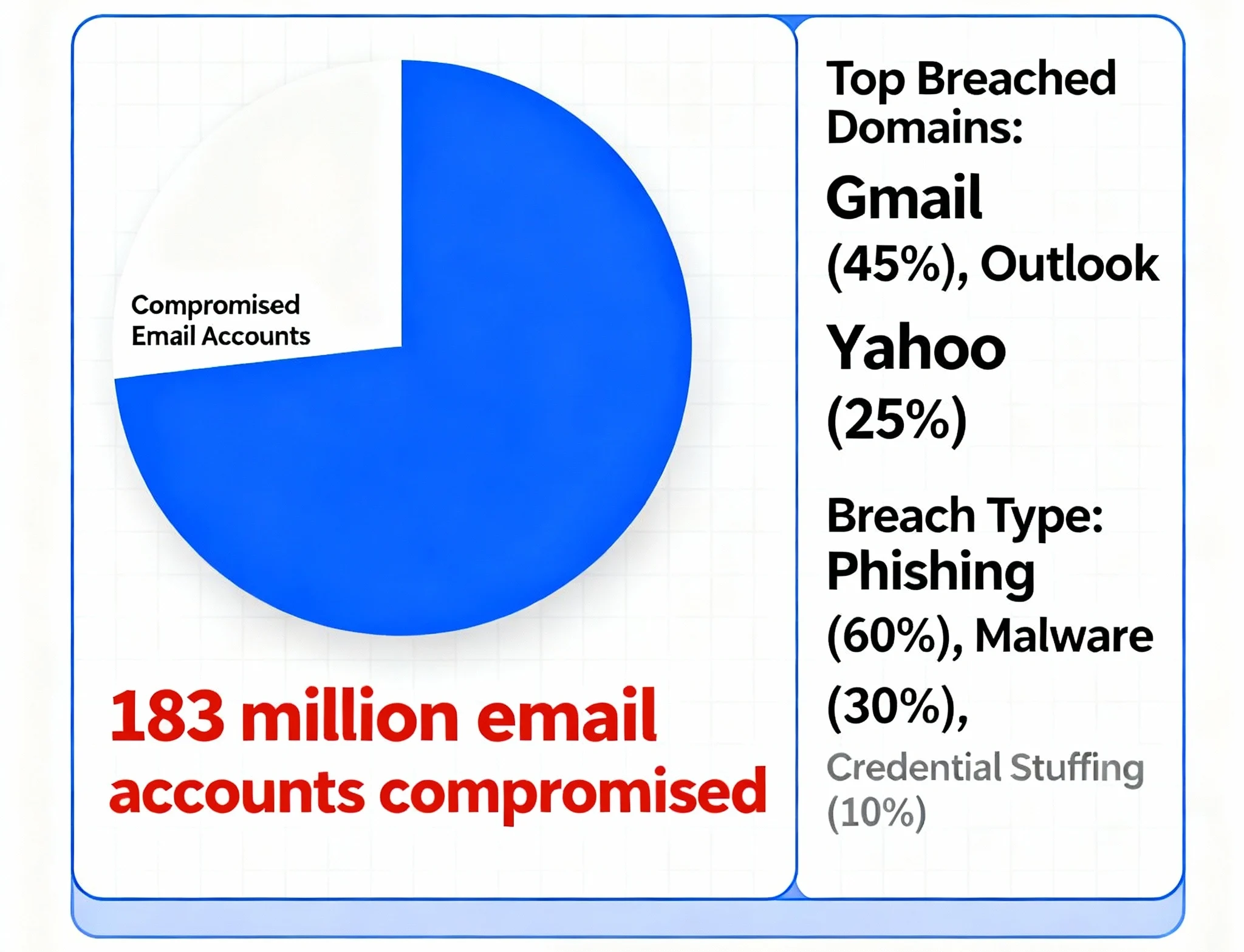
Statistics of the data breach
Discovery of the Breach
Synthient LLC compiled the breached database from logs created by infostealer malware that infected personal devices worldwide. Security platforms confirmed the leak was not from Google’s servers nor any single corporate infrastructure. The threat instead emerged as malware intercepted users’ passwords—exposing millions of Gmail accounts among other platforms like Apple and Facebook. Industry analysts stressed the increased risk level because exposed credentials included both web addresses and plain text passwords.
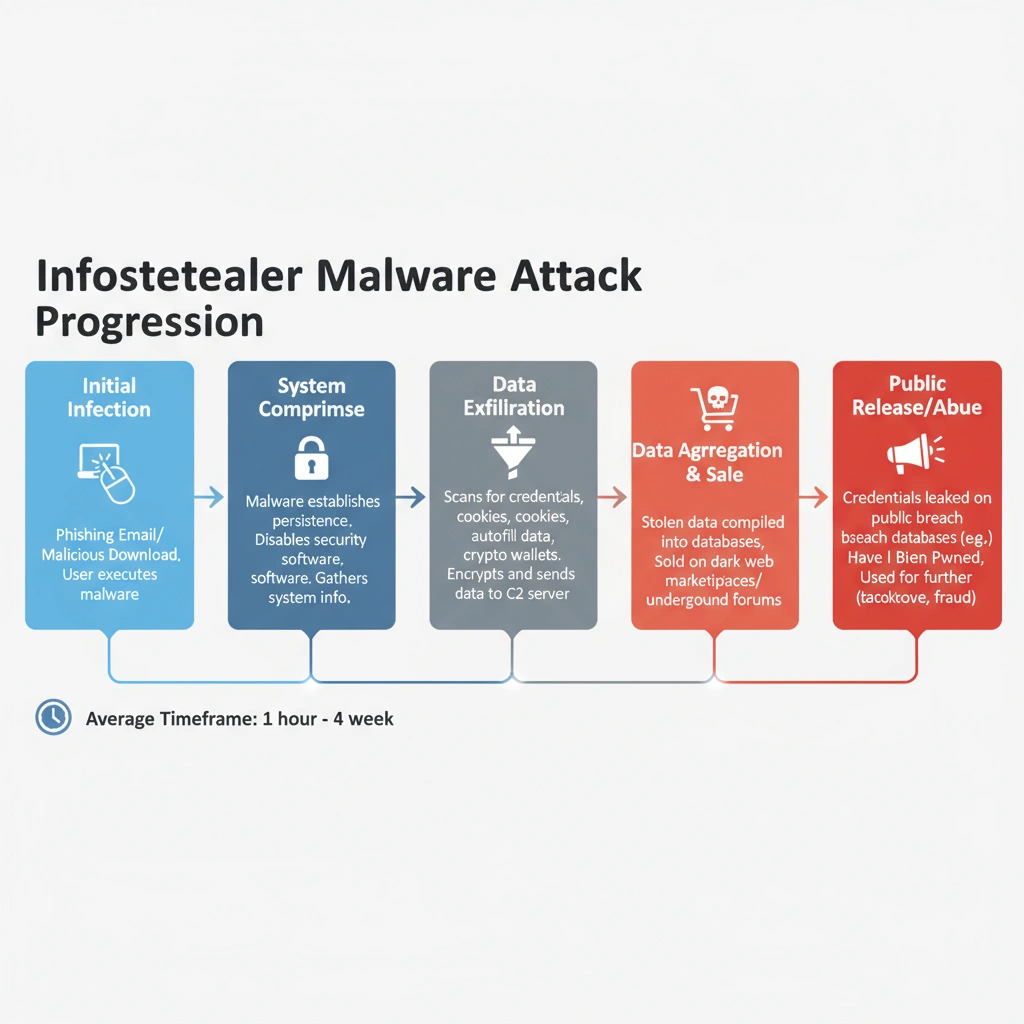
Timeline showing how infostealer malware led to the credential database breach
Scope and Impact
Breached credentials appeared almost instantly across criminal marketplaces and underground channels, indicating a rapid movement into cybercrime networks. The magnitude of this event places users at heightened risk for credential-stuffing attacks and identity theft, especially where passwords overlap between platforms. Many analysts describe this as one of the largest credential leaks in history, citing the scale and real-time exposure. The dataset added to Have I Been Pwned on 21 October 2025 enables individuals and companies to check if their accounts appear in breach logs.
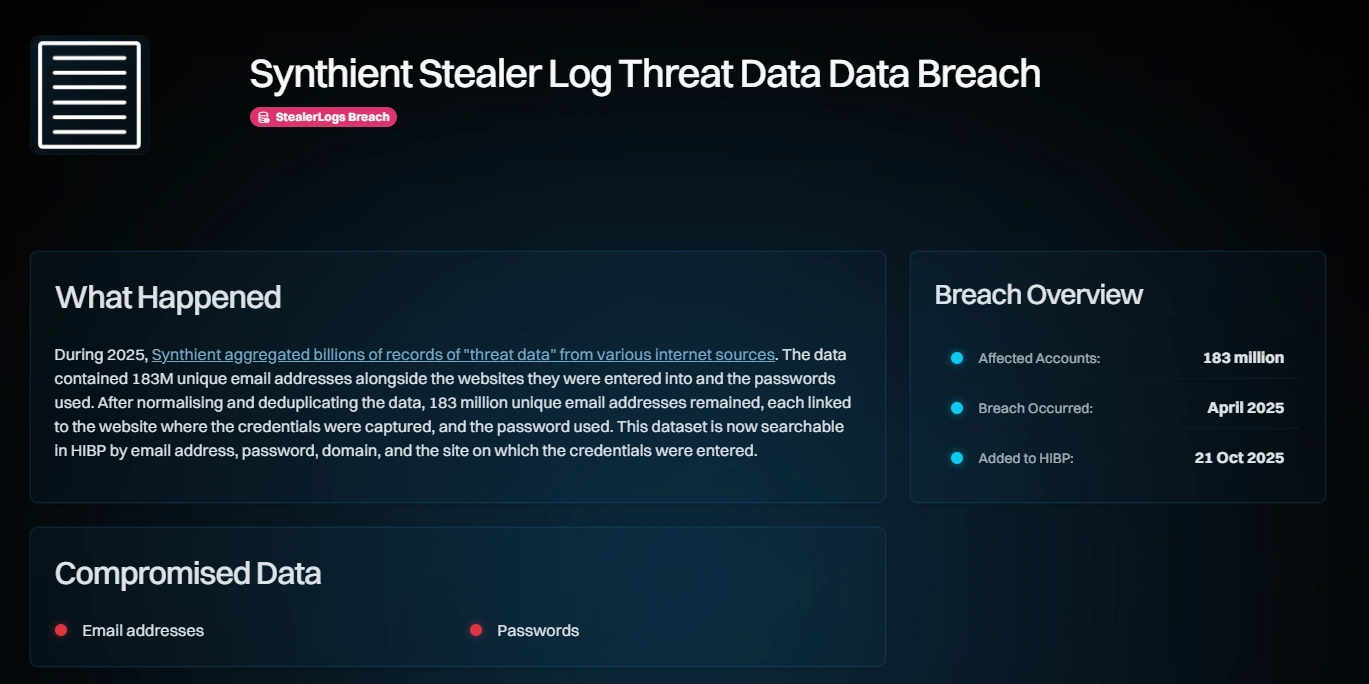
Users can check the breach data from Have I Been Pwned
Vulnerability of Gmail Accounts
Gmail users are a primary target within the new database, with substantial numbers confirmed in plaintext listings. Security teams analysed logs from info-stealer malware, finding that attackers captured more than just passwords. Some logs added authentication tokens and browser session cookies, making standard two-factor prompts easier for criminals to bypass. However, as of writing, no evidence indicates Gmail’s infrastructure has suffered compromise directly. Instead, malware on personal devices siphoned the data.
Warnings and Expert Advice
Troy Hunt, founder of Have I Been Pwned, addressed public concerns by confirming that the new breach features fully searchable records by email, domain, and password. Analysts and cybersecurity professionals recommend immediately resetting passwords and activating two-step verification on all related accounts. Hardware keys and passkeys are advised over SMS codes for higher security levels, with browser security and device protection now critical for safe digital life.
Recommendations for Individuals and Organisations
Experts urge every Gmail user in Australia and globally to run Google’s Security Check-up as soon as possible. The check-up tool can identify unfamiliar devices, connected apps, and session tokens that should be removed. Password reuse becomes a key vulnerability, with specialists advising unique strong passwords for every service. Multi-factor authentication must be enabled everywhere, and security teams should enforce regular audits and remedial steps. Companies should treat the breach as a credential exposure event, reset passwords enterprise-wide, and revoke all legacy authentication methods.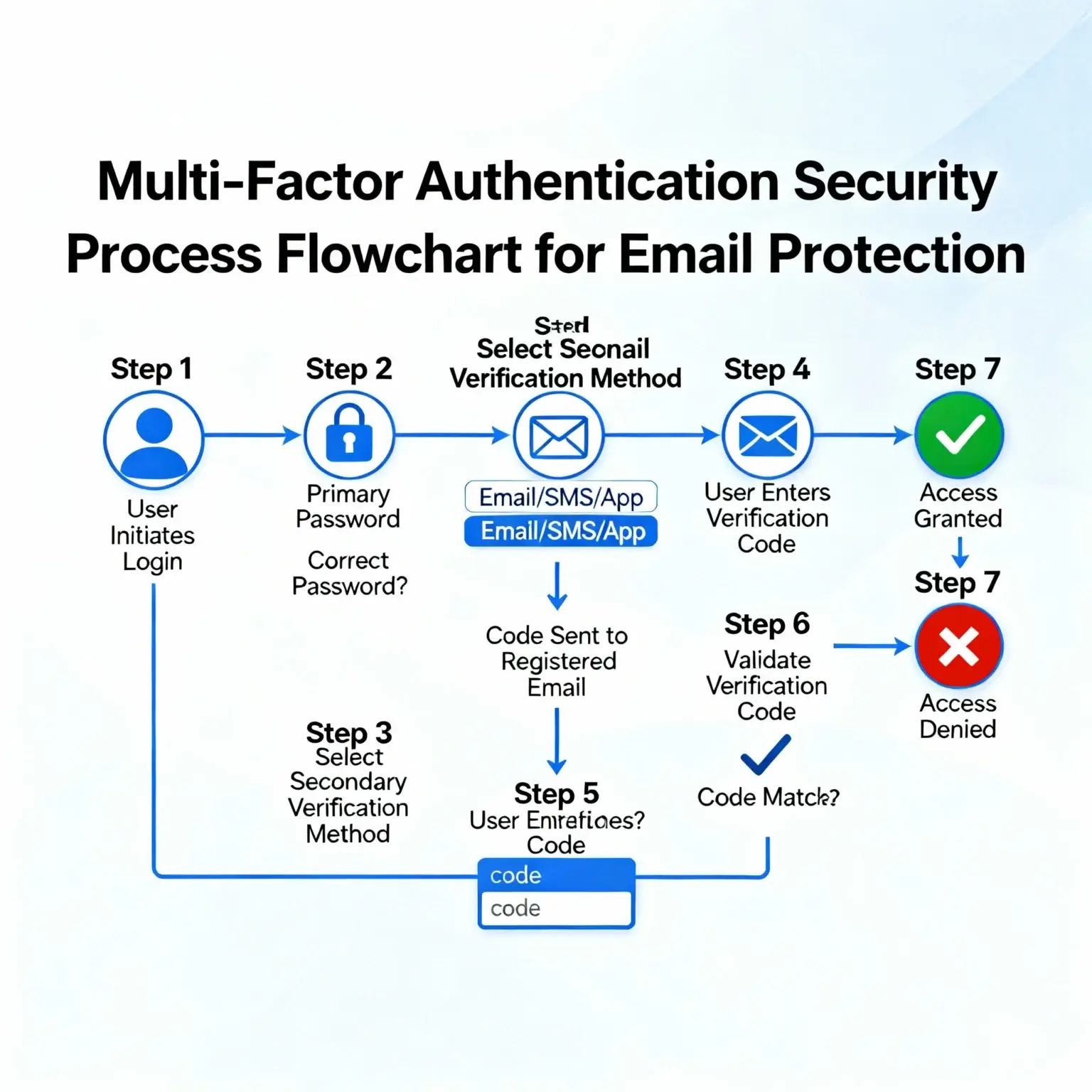
Step-by-step guide showing multi-factor authentication workflow for account security
International Cybersecurity Response
Security teams believe the Synthient Stealer Log Threat Data sets a new benchmark in credential leak scale and methodology. The breach highlights an evolving trend where infostealer malware overtakes classic system hacks as the most damaging vector of credential loss globally. Organisations using Gmail or Google Workspace are now advised to enforce multiple authentication protocols and enhance malware monitoring across their fleets. International cyber agencies continue to track the source and distribution mechanisms, releasing alerts as new information surfaces.
Actions for Australian Gmail Users
Australian cyber authorities advise all affected users to respond quickly and safeguard their digital identities. Immediate password changes, activation of multi-factor authentication, and review of account activity stand as primary steps recommended by official security advisories. Cybersecurity analysts recommend using anti-malware tools, verifying devices for infection, and checking breach-monitoring platforms such as Have I Been Pwned for ongoing updates. Organisations must conduct fleet-wide security audits, enforce password resets, and educate personnel about contemporary malware risks.

Security checklist for protecting accounts after a credential breach
Prevention for Future Attacks
Experts agree malware-driven breaches can be mitigated by strong device security practices and awareness programs targeting staff and end-users. Regular training and monitoring of network activity safeguard against info-stealer campaigns that exploit browser vulnerabilities or weak authentication methods. Cybersecurity teams highlight the need for quick action and continuous vigilance as credential theft trends reshape global risk profiles.
Ongoing Investigation and Updates
Authorities and platform owners continue investigating the source and reach of the Synthient breach. Reports emphasise the pivotal shift away from single-platform compromises towards multi-service credential theft via infostealer malware. Platforms such as Have I Been Pwned and various dark web monitors have made the dataset searchable so users can verify exposure and total risk.
Also Read: Microsoft 365 Price Hike Sparks ACCC Legal Battle Over Consumer Rights
Official Statements
Troy Hunt released a statement on the matter: “The newly disclosed data includes website URLs, email addresses, and passwords. These consist of both ‘aler logs credential stuffing’, featuring confirmed Gmail login details.” Organisations across industries are aligning with cybersecurity analysts in urging strong password management and multi-factor authentication activation. No further official comment from Google confirms server compromise, but global advisories continue encouraging caution and regular account review.
Summary
The confirmation of Gmail account passwords in the 183 million user breach marks a turning point in global cybersecurity practices. Australian users and organisations must act now by changing passwords, boosting authentication protocols, monitoring accounts, and remaining vigilant against ongoing malware threats. The incident illustrates how user security depends on both provider infrastructure and strong personal device management, with continuous adaptation crucial as cyber adversaries evolve.