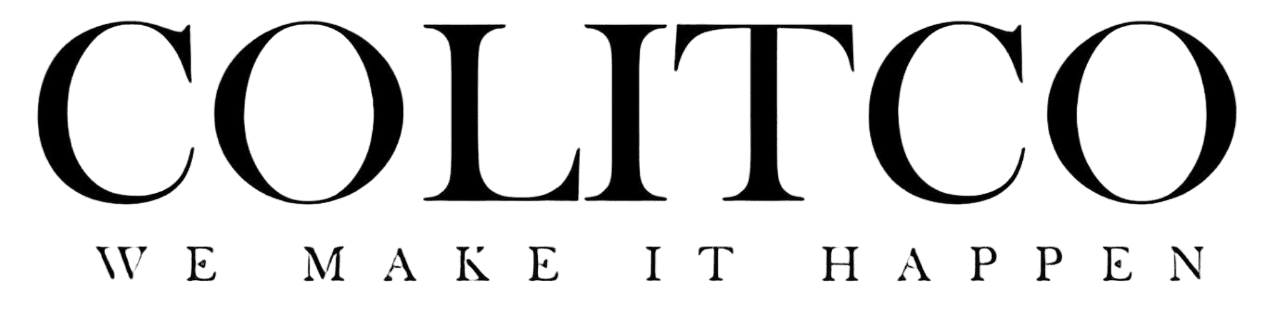Australian mining cybersecurity has become a top concern in 2025 with the onset of growing digital threats faced by operators. It is among the country’s critical infrastructure sectors and remains a prime target for ransomware syndicates and adversarial forces. This year, cases were said to have established that mining contractors and companies were hit by sophisticated breaches, prompting the industry to put security into all aspects of its operations.

Digital systems are now central to Australian mining, but they also expose critical infrastructure to cyber threats.
Australian mining is increasingly virtual, reliant on networked infrastructure to find, remove, transport materials, and track safety. These technologies make operations more efficient, but create threats that threat actors are leveraging. The convergence of operation technology and information technology has expanded attack surfaces, so that cybersecurity is required for the reliable functioning of mining operations.
More Cybersecurity Incidents in Australian Mining
In 2025, there were at least five reported cybersecurity incidents of Australian mining-related companies. Pressure Dynamics International, which is a resource business contractor, was one of them and was attacked by a group of ransomware. The attack demonstrated that attackers usually use contractors and suppliers to enter larger operations.
Ransomware attacks in 2025 have targeted contractors and suppliers, creating new vulnerabilities for the mining sector
The mining industry depends heavily on contractors related to engineering, logistics, and others. The attackers take advantage of the dependency by hacking smaller firms with weaker security before attempting to hack larger mining networks. The incidents are used to underscore the risk that comes with complex supply chains and the importance of effective security measures by third parties.
Australia’s Role within the Global Threat Environment
Australia ranked third globally for the threats of cyber in 2025. Mining and minerals were among the industries most exposed. It is an indication of activity from financially motivated groups and state-sponsored groups looking to disrupt critical industries.
Threats extend beyond traditional IT infrastructure today. Operational technology, sensors, and Internet of Things devices are regularly targeted. These platforms govern drilling, transportation, ventilation, and safety functions.
Australia ranked third globally in 2025 for cyber threats to critical infrastructure, including mining and resources.
When they are compromised, production can halt, danger can be caused, and worldwide supply chains are affected. Since Australia is a large exporter of minerals, attackers see disruptions at mines as a means to exert power across international borders.
Vulnerabilities in Operational Technology
Australian mining operational technology continues to be vulnerable as it was developed using outdated designs. The majority of the OT systems were not built to withstand cyber attacks, but currently operate in tandem with digital instruments. This integration has rendered spaces both effective and susceptible to compromise.

Operational technology in mining remains vulnerable as legacy systems are increasingly connected to digital networks.
Off-site mining operations also present extra challenges. Rural mines prefer to implement centralized, automated systems that can be accessed from major urban areas. Even though remote monitoring lowers costs and enhances effectiveness, it leaves the gates open for hackers. Regulators have called for closer network separation and access control to minimize exposure.
Current Threat Trends in 2025
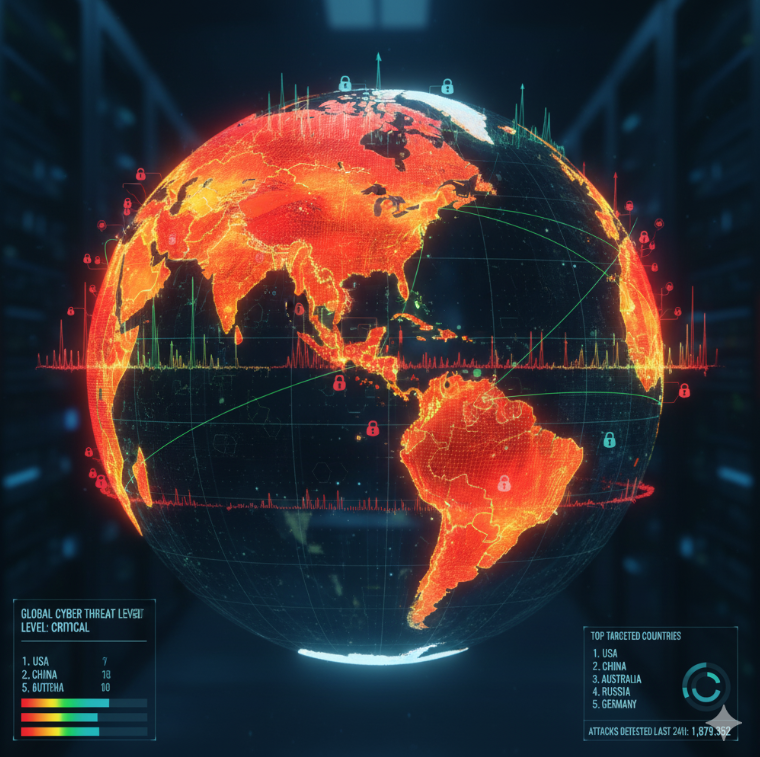
In July 2025, a security review gave the most frequent threat to mining as ransomware. Attacks to capture access to remote access machines and phishing campaigns were identified as typical attack techniques. This is in accordance with the trend of the world, but poses a particular threat to Australian mining because it relies on networked infrastructure.
Phishing, ransomware, and breaches of remote access infrastructure are recurring threats against Australian mining firms in 2025.
Companies are fighting against these vulnerabilities by implementing global standards such as IEC 62443, which give a detailed guideline on how to secure industrial control systems. Other organizations are even experimenting with artificial intelligence solutions, which detect out-of-the-ordinary behavior of the system. The applications study real-time data and send early warnings before problems develop into serious disruptions.
Data Protection Strategies in Mining
Data protection is growing to be front and center of mining cybersecurity. Companies are creating immutable copies that cannot be modified by hackers, ensuring recoverability when ransomware locks up key systems. Offline storage is also being used to protect sensitive files from remote attacks.
Training of employees is also given a focus. Employees are being instructed on how to spot phishing attacks, protect credentials, and report suspicious activity. Human error remains the most common entry point for attackers. All these measures aim to build resilience across all levels of the organization.
Strengthening Cybersecurity Through Strategic Measures
In 2025, mining companies implemented multi-layered security measures to enhance safety. Multifactor authentication and privilege limits have been utilized to limit access to systems. Network segmentation is currently applied comprehensively to segregate operational technology from internet-facing systems, limiting the scope of intruders laterally moving.
Vendor risk management has also increased. Service providers are now being included with cybersecurity requirements in their contracts, and monitoring and regular audits are performed. Because hackers typically attack contractors, this measure is an important move towards filling the gaps in the supply chain that existed before.
Market Developments and Industry Partnerships
Cybersecurity services need to escalate sharply in 2025, and this was mirrored in a radical market change. Accenture’s billion-dollar acquisition of CyberCX was a watershed for Australia’s cybersecurity sector. This acquisition has created one of the most influential cybersecurity service companies in the country, which can service industries like mining that remain vulnerable.

The 2025 acquisition of CyberCX by Accenture marked a major consolidation in Australia’s cybersecurity sector.
Such a merger provides mining operators with increased resources and know-how. The alliances with providers of such stature will be paramount as threats continue to evolve. The purchase also suggests that international players view the security of Australia’s critical infrastructure as a leading and growing market.
Securing Operational Technology Systems
By October 2025, interest in protecting cyber-physical systems in mining had picked up. Drilling platforms, equipment, and driverless transport systems remain very vulnerable to attacks. The challenge lies in getting the correct balance between operational performance and additional security measures.

Automated transport and drilling systems are vulnerable to cyber intrusions, driving the adoption of OT intrusion detection tools.
Mining firms have started installing intrusion detection systems specifically designed for OT environments. These systems monitor internal network traffic and alert operators to anomaly patterns. In combination with incident response planning and regular drills, this practice helps companies minimize disruptions at a minimum in case breaches occur.
Industry-Government Collaboration
In 2025, the Australian government, through the Australian Cyber Security Centre, enhanced assistance to the mining sector. The businesses are encouraged to report quickly so that industry partners may learn from one another about how to counter the threats. The shared knowledge keeps the same attacks from being used against multiple operators.

Government and industry collaboration is strengthening mining’s resilience against evolving cyber threats.
New frameworks are being aligned with critical infrastructure regulations to enable compliance with the strengthening of resilience. With collaboration with government agencies, mining companies are strengthening strategies for protecting their operations as well as the economy in general.
Addressing the Human Factor
Human error is still a leading cause of cyber attacks in Australian mines. Phishing e-mails are still a favorite attack method and typically serve as the entry point for attackers to gain access to corporate networks. Training sessions now simulate real-time scenarios to help employees effectively deal with them.
Executives are also being given cybersecurity news so that security is kept in mind while making decisions. Organizational-wide awareness lessens reliance on technical controls only, making a more robust defense overall.
Future Cybersecurity for Mining
Australian mining cybersecurity will remain a many-faceted problem. Offenders are still becoming increasingly sophisticated, often pairing malware with social engineering to attack human and technical weaknesses together.
However, sustained investment in surveillance equipment, staff training, partnership with specialist providers, and closer partnership with the government suggest resilience will be increased. The capability of the industry to evolve with changing threats will suggest whether the industry will continue operations at full capacity in the future.
Also Read: Commonwealth Bank Fixes ‘Issue’ Affecting Payments, Online Access and ATMs
Final Thoughts
Cybersecurity is presently an imperative in Australian mining for the protection of running critical infrastructure. In 2025, ransomware, phishing, and intrusions into operational technology have affected contractors and mining companies.
The industry has responded by being more regulated in controlling access, managing vendors, enhancing surveillance systems, and regularly training employees. The consolidation of the market and government benefits, such as historical acquisitions in the cybersecurity industry, have also contributed to the strength of the industry.
With digital integration of mining operations going into the future, cybersecurity will remain a required component in assets, employees, and the economy’s security. The achievements by the year 2025 depict the industry that addresses the most burning issues.
FAQs on Cybersecurity in Australian Mining
1. What does cybersecurity mean in the context of Australian mining?
Cybersecurity in mining refers to safeguarding digital and operational systems that run extraction, logistics, workforce safety, and data platforms. It ensures critical infrastructure continues to function without disruption from malicious actors.
2. Why is the mining sector a prime target for cyberattacks?
Mining is classified as critical infrastructure under Australian law. It supports exports, energy supply, and defence supply chains. Disrupting mining operations can have economic and national security consequences, making the sector attractive to attackers.
3. What were the most common cyberattacks on mining companies in 2025?
Reports in 2025 confirmed ransomware, phishing, credential theft, and supply chain breaches as the most common forms of attack. Contractors and partners were often targeted as entry points into mining systems.
4. How many cyber incidents affected Australian mining companies in 2025?
At least five incidents were reported in FY2025 involving mining-related companies and contractors. This number reflects only those publicly disclosed, meaning the actual figure may be higher.
5. Why are supply chains such a weak point for mining companies?
Mining firms depend on a wide network of service providers. Attackers target smaller contractors with weaker security to move into larger organisations. This tactic was evident in the Pressure Dynamics International ransomware listing in 2025.
6. What role does operational technology play in mining cybersecurity risks?
Operational technology (OT) controls machinery, drilling, and transport systems. Many OT systems were built without modern security features and are vulnerable when connected to IT networks.
7. How is the Australian government supporting mining cybersecurity?
The government, through the Australian Cyber Security Centre (ACSC), shares threat intelligence, incident reporting frameworks, and compliance requirements under the Security of Critical Infrastructure Act. Mining operators are also encouraged to join information-sharing initiatives.
8. What legal obligations do mining companies face regarding data protection?
Mining firms handling employee or contractor information must comply with the Privacy Act 1988. They must also report notifiable data breaches. Under critical infrastructure laws, they are required to assess and manage cyber risks.
9. What steps are mining companies taking to protect operational systems?
Companies are segmenting IT and OT networks, adopting IEC 62443 standards, and deploying intrusion detection tools tailored for industrial environments. These steps limit attackers’ ability to move across systems.
10. How is the mining industry addressing the human factor in cybersecurity?
Firms have rolled out phishing simulation exercises, employee awareness programs, and executive briefings. Since human error is a leading cause of breaches, building cyber awareness is now a priority.
11. Which market developments in 2025 are shaping mining cybersecurity?
Accenture’s acquisition of CyberCX for $1 billion was one of the year’s biggest security deals. It expanded expertise and resources available to industries like mining facing continuous attacks.
12. How can mining companies manage cyber supply chain risk?
Firms are introducing supplier risk assessments, contract clauses mandating cybersecurity controls, and audits of vendor practices. The ACSC also advises using supplier cyber risk management frameworks.
13. What international standards are used in mining cybersecurity?
Standards such as IEC 62443 (for industrial control systems) and NIST Cybersecurity Framework are being adopted. They provide structured methods for asset inventory, segmentation, monitoring, and recovery planning.
14. What future trends could affect cybersecurity in mining?
Experts expect continued growth in ransomware attacks, expanded use of AI-driven defence tools, and increased regulatory oversight. Remote operations and digital twins will also introduce new vulnerabilities.
15. How does cybersecurity protect Australia’s economy through mining?
By safeguarding production systems and supply chains, cybersecurity ensures reliable mineral exports, stable operations, and protection of national critical infrastructure. It supports Australia’s standing as a global resources leader.